The Wall of Trust - Security in the Cloud
Not long ago consumers were hesitant to enter credit card information into an encrypted Web page. However, the convenience of online shopping was too compelling to ignore. Initial hesitation was replaced with caution and a bit of blind trust. As online shopping matured, acceptance came with the understanding that security risks are manageable by following best practices. Successful companies placed top priority on securing their customer's personal data, developed comprehensive security policies, introduced automation, and stayed vigilant by conducting periodic audits. The same evolution is taking place in IoT.
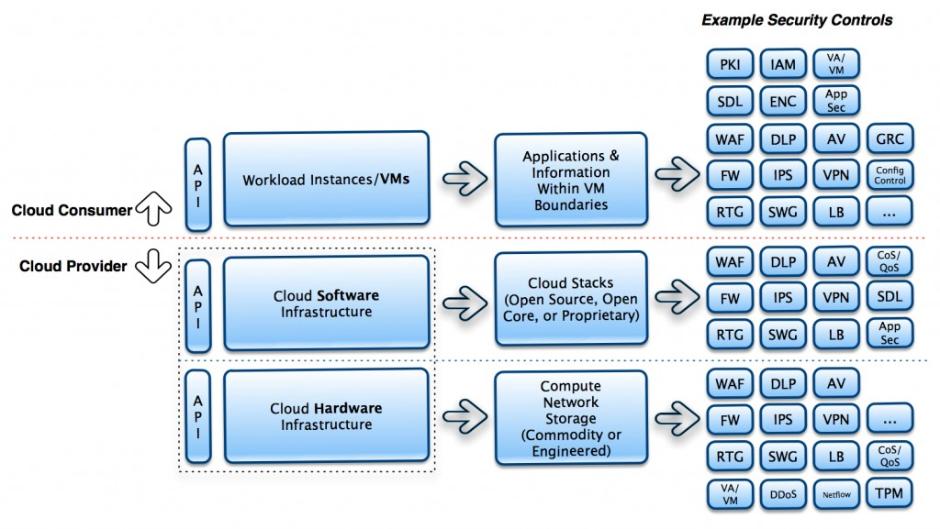
Because we are infrastructure specialists: performance, security and high availability are always our top priorities. Business continuity figures prominently into our risk management strategy. Every IoT project we design undergoes the creation of a baseline performance and security standard and establishes a service commitment to senior management called The Wall of Trust.
The Wall of Trust embodies F/H/C's library of security controls and best practices that certifies our IoT infrastructure solutions adhere to the highest standards in the industry, including: HIPAA, PCI-DSS and FISMA.
We provide certification capable of withstanding third-party audits by combining hardware security methods like Intel's Trusted Execution Technology with VMware virtualization and RSA security tools.
Standardization plays an important role in keeping security manageable and your company data safe. Compression, encryption and VPN tunneling protocols have matured to provide secure connectivity across the WAN, liberating data from being locked down to a single computer. However, you always maintain final authority over where your data can reside. That's the F/H/C advantage.
Robust solutions and multiple redundancies will enable you to run your IoT applications in confidence. As a general rule, we partner with IoT service providers that have higher data center security standards and more certified experts on staff than most internal IT departments at Fortune 500 companies. The integrity of your company data is further guarded by iron-clad SLAs.
Security. We take it seriously.